Disclaimer – These Apps Are For Pentesting and Security Purposes, We discourage Non-ethical use of these apps, MyHacker and App Developers won’t be responsible...
Network
Introduction: Kali Linux is a popular Linux distribution used by ethical hackers, security professionals, and penetration testers worldwide. It is known for...
Introduction: With the proliferation of digital media, it’s becoming increasingly important to have easy access to all of your files, whether...
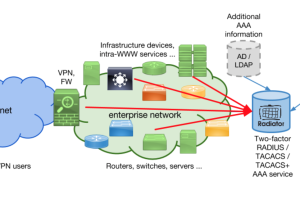
Introduction If you work with network devices, you have likely heard of TACACS (Terminal Access Controller Access Control System). TACACS is a network...
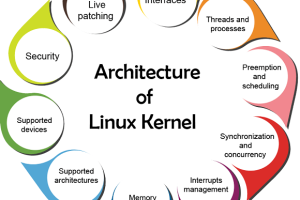
Introduction: Insmod is a command-line utility that is used to load kernel modules into a running Linux kernel. Linux is known for its modular design, and...
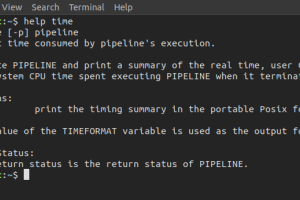
The system time on a Linux machine is stored as the number of seconds since the Unix epoch (January 1, 1970, 00:00:00 UTC). You can display the current system...
Network performance assessment is a critical task for system administrators. System admins are often required to master more than one Linux network monitor...
In today’s fast-paced and highly interconnected business environment, remote access has become an essential requirement for many organizations. Employees...
The word hacker itself has a negative impression. But there are people out there working upon finding security flaws and exploiting them in order to improve...
In the modern world, data is one of the main driving forces. Simply put- data is important. One of the best ways to store data is by using Linux NAS(Network...