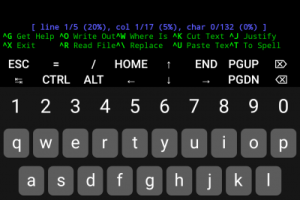
There are many Termux hacking tools online, but be wary when downloading. Some may simply be clickbait or force users to install malware onto their devices...
Security
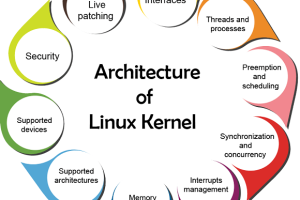
Security-Enhanced Linux (SELinux) is an access control mechanism in the Linux kernel that provides security policies. While it’s an effective tool that...
Disclaimer – These Apps Are For Pentesting and Security Purposes, We discourage Non-ethical use of these apps, MyHacker and App Developers won’t be responsible...
Introduction: Kali Linux is a popular Linux distribution used by ethical hackers, security professionals, and penetration testers worldwide. It is known for...
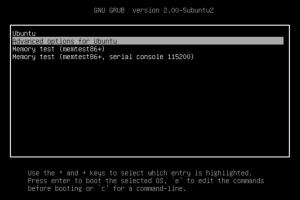
Introduction Grub (Grand Unified Bootloader) is a popular bootloader used in most Linux systems. It is responsible for loading the operating system into the...
Introduction: Insmod is a command-line utility that is used to load kernel modules into a running Linux kernel. Linux is known for its modular design, and...
There might be many reasons for your Linux file system to go into unusable or corrupted state. Such as: Sudden power failure, faulty device drivers, faulty...
Your android devices can be Identified in multiple ways when accessing certain services and networks. Almost every different service associated with your...
Network performance assessment is a critical task for system administrators. System admins are often required to master more than one Linux network monitor...
In today’s fast-paced and highly interconnected business environment, remote access has become an essential requirement for many organizations. Employees...