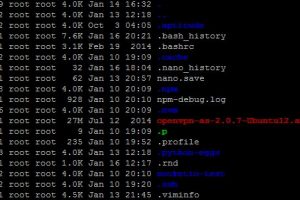
Security is a big concern for Linux. That’s why learning to manage Linux file permissions is essential. As Linux is used in mainframes and servers, it is...
Security
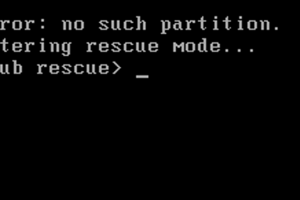
There might be many reasons for your GRUB rescue mode to show up. Such as you accidentally deleted the Linux partition in multi-boot operating system...
Here we tried to list out all the possible things you should consider when choosing between PostgreSQL vs MySQL for a given application or given sets of...
The embroidered flexibility of Linux makes it an ideal platform for coding and software development. But you have so many choices between Linux distribution...
The word hacker itself has a negative impression. But there are people out there working upon finding security flaws and exploiting them in order to improve...
Kali Linux comes to android with the help of a simple and easy to use app called Bochs. In this article we will show you how to install and use Bochs and give...
According to OWASP, SQL injection is one of the top 10 most commonly found vulnerabilities in web applications. In this tutorial we are going to show you how...
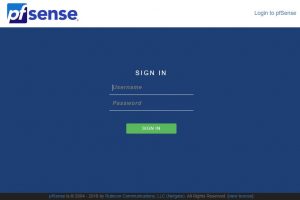
pfSense is one of the most versatile firewall systems available out there in the market. It uses BSD as its base operating system. pfSense is based on...
There are multiple scenarios where you will be required to reset Cisco router password without knowing it. For example if your network administrator left the...
What is Vulnerability assessment? When Securing organization’s assets, knowledge is power. In today’s world as businesses grow, their dependency on...