Introduction
If you work with network devices, you have likely heard of TACACS (Terminal Access Controller Access Control System). TACACS is a network authentication protocol that provides centralized authentication and access control for network devices. It is widely used in enterprise networks, particularly in Cisco environments. In this article, we will provide a comprehensive guide to TACACS, including its definition, benefits, and how to use it in your network infrastructure.
Also read: Bash Strings
What is TACACS?
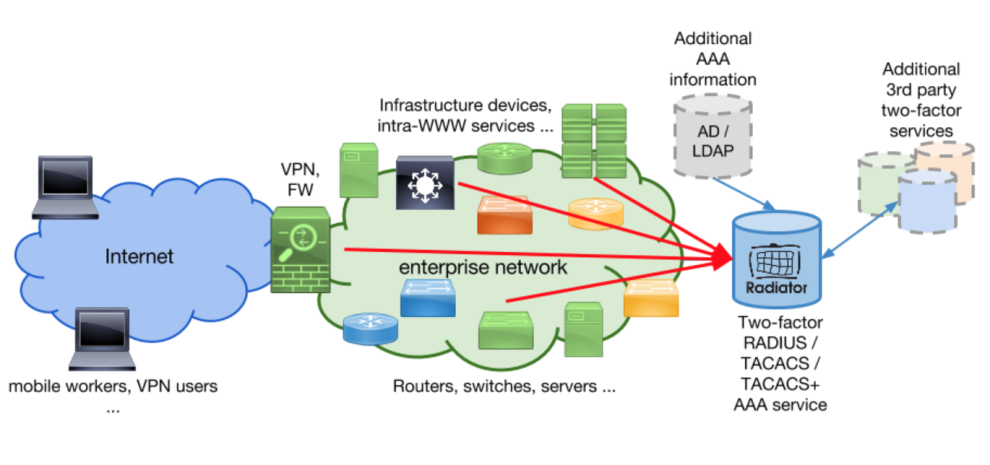
TACACS is a network authentication protocol that provides centralized authentication and access control for network devices. It was initially developed by BBN Technologies for the Department of Defense (DoD) in the 1980s. TACACS separates authentication, authorization, and accounting (AAA) functions into three separate services. The TACACS protocol is implemented as a client-server architecture, where network devices act as clients and TACACS servers provide authentication and access control services.
Benefits of TACACS
TACACS provides several benefits, including:
- Centralized authentication and access control: TACACS servers act as a central point for authentication and access control, which simplifies management and reduces the likelihood of security breaches.
- Fine-grained access control: TACACS provides granular access control, allowing administrators to control access to specific commands and features based on user roles and privileges.
- Accounting and auditing: TACACS provides detailed accounting and auditing capabilities, allowing administrators to track user activity and detect potential security breaches.
- Scalability: TACACS is highly scalable and can support large enterprise networks with thousands of network devices.
How TACACS Works
TACACS separates AAA functions into three separate services: authentication, authorization, and accounting. When a user tries to access a network device, the device sends an authentication request to the TACACS server. The TACACS server then sends an authentication request to an external authentication server, such as RADIUS or LDAP. If the authentication is successful, the TACACS server sends an authorization request to an external authorization server, such as Active Directory. The authorization server then determines the user’s privileges and sends them back to the TACACS server. Finally, the TACACS server grants or denies access to the network device based on the user’s privileges.
How to Implement TACACS in Your Network Infrastructure
To implement TACACS in your network infrastructure, you will need to follow these steps:
- Install and configure a TACACS server: There are several open-source and commercial TACACS servers available, including FreeTACACS+ and Cisco Secure ACS. You will need to install and configure the TACACS server to support your network devices and external authentication and authorization servers.
- Configure your network devices to use TACACS: You will need to configure your network devices to send authentication and authorization requests to the TACACS server. This can typically be done through the device’s command-line interface (CLI) or web-based interface.
- Configure your external authentication and authorization servers: You will need to configure your external authentication and authorization servers, such as RADIUS or LDAP, to support TACACS authentication and authorization requests.
Conclusion
TACACS is a powerful network authentication protocol that provides centralized authentication and access control for network devices. It separates AAA functions into three separate services, providing granular access control and detailed accounting and auditing capabilities. By implementing TACACS in your network infrastructure, you can simplify










Add Comment