User authentication is essential for security of any web application. All the security parameters like captcha and limiting the login attempts should be set while constructing a user authentication system. If these parameters are not defined properly, the attacker can perform brute force attack on a login form and steal credentials. This guide will walk you through the process of brute forcing the login form step by step. So Fire up your Kali Linux and follow these steps to brute force login page.
Brute force login page
Getting the web form post parameters
In order to attack the web form first we need to get the web form’s login field post parameters and find out how login page responds to failed logins. Key parameters that we need to obtain are
- IP Address of the website
- URL
- type of form
- field containing the username
- field containing the password
- failure message
We can get these parameters by using Burp suite or Temper Data. You can open burpsuite by going to Applications -> Kali Linux -> Web Applications -> Web Application Proxies -> burpsuite.
For sake of this tutorial we will be attempting to crack the password on the Damn Vulnerable Web Application (DVWA). You can run it from the Metasploitable operating system and then connect to its web page.
Next we will attempt to get all these POST parameters from the login page form. We need to enable the Proxy and Intercept on the Burp Suite like shown below in the image.
Now we need to configure our browser to use the proxy settings. go to Edit -> Preferences -> Advanced -> Network -> Settings(in Firefox)
Configure your browser to use localhost(127.0.0.1) as a proxy and use 8080 as a port.
Get the Bad Login Response
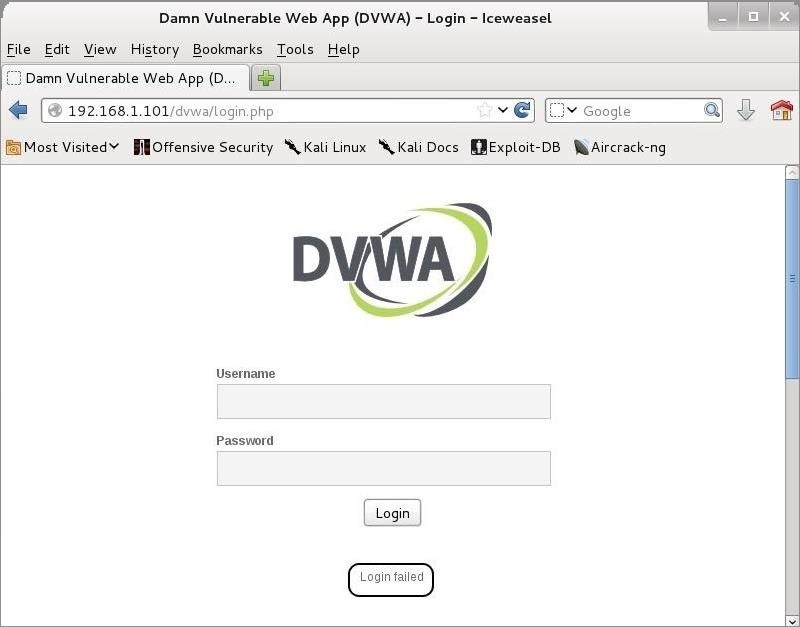
Now try to login with wrong username and password on a login page. Now the burpsuite will show us the key fields that we need to use in hydra to crack the password.
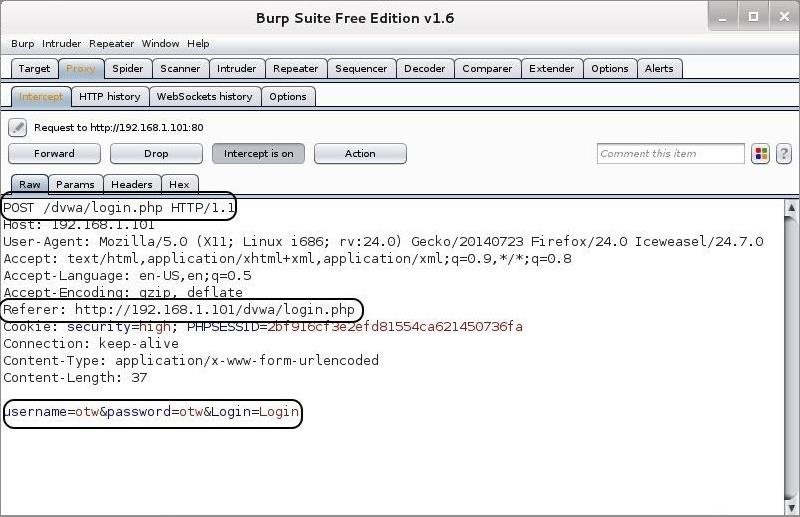
After obtaining the necessary info, forward the request from Burp Suite by hitting the “Forward” button on the far left . The DVWA returns a message that the “Login failed.”
Using hydra to brute force login page
Now we are going to use this collected information in hydra and try to crack the password. basic syntax structure for hydra is given below.
#hydra -L <username list> -p <password list> <IP Address> <form parameters><failed login message>
So based on the information that we got from burp suit analysis our command should look like this:
#hydra -L <wordlist> -P<password list> 192.168.1.101 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed"
Wordlist
Last thing that we need is a wordlist to crack the password. You can scour the internet for wordlists, you will find wordlists that may be upto 100 GB. But Kali Linux also has inbuilt wordlists. You need to issue the following command in terminal to find all of them.
#locate wordlist
For the sake of simplicity we will use the following wordlist.
/usr/share/dirb/wordlists/short.txt
Now, let’s build our Final command with all of these elements, as seen below.
#hydra -l admin -P /usr/share/dirb/wordlists/small.txt 192.168.1.101 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed" -V
Since we used the –V switch, THC-Hydra will show us every attempt. Next step is to get back and grab a cup of coffee while password is being cracked.
Also check out our list of hacking tools
Here is a list of some important Command Line argument used in hydra
- -l indicates a single username (use -L for a username list)
- -P indicates use the following password list
- http-post-form indicates the type of form
- /dvwa/login-php is the login page URL
- username is the form field where the username is entered
- ^USER^ tells Hydra to use the username or list in the field
- password is the form field where the password is entered (it may be passwd, pass, etc.)
- ^PASS^ tells Hydra to use the password list supplied
- Login indicates to Hydra the login failed message
- Login failed is the login failure message that the form returned
- -V is for verbose output showing every attempt
If you have any doubts please let us know in the comments section.











Add Comment